In recent years, ISPs here in Nepal have started deploying IPv6 in their network. For users who have a Linux server with tons of self-hosted things, this is a godsend feature. With IPv6 there is no need for NAT and any sort of complication. You just expose a port and make some firewall rules and you are ready to go.
In the case of Worldlink, it's the same. But the thing with Wordlink's CPEs is they haven't enabled any sort of firewall. This means all of the inbound and outbound traffic for the IPv6 is allowed. That means the devices have to protect themselves with their built-in firewalls. I am guessing they are doing this because they don't allow router access to the customers and users who want to add firewall rules for their IPv6 would have to contact them, which I am sure will be troublesome. So, they thought of letting it all in without thinking about the security consequences.
Too much restriction was also not my liking so I thought about getting a secondary router. I had a fair share of experience using and installing OpenWRT as previously I did a lot of experiments installing it on TP Link routers. But it was 2023, so I had to look in the market for some better routers with good support for the OpenWRT.
During my search, only one router popped up everywhere. It was Xiaomi's Mi Router 4A Gigabit. It had a decent processor, RAM was 128 MB and Flash Memory was 16 MB. What caught my eye was the RAM, that's really good.
So I bought one. Installed OpenWRT on it using this method, and got it running within a few minutes.


Now setting up the IPv6 was really a tricky part. Since my ISP provides a dual-stack IP, meaning I get IPv4 and IPv6 together. But the thing is, IPv4 is NAT and has no problem with me again putting it behind another network. But for IPv6 to work in such a way that every user connected to the Mi Router gets a public IPv6, the interface for IPv6 has to be set in a relay mode.
To set the interface to the relay mode. Just go to the network interfaces.
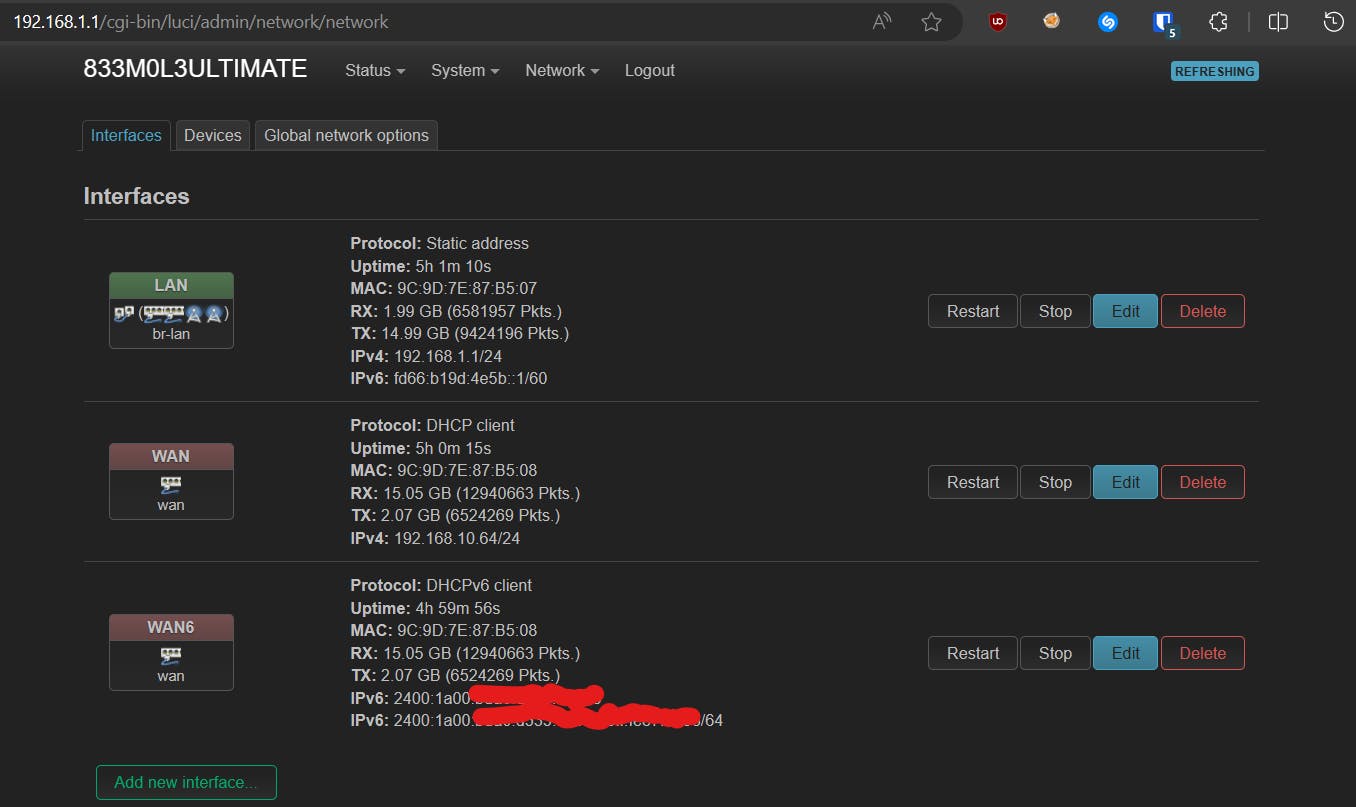
Edit your IPv6 WAN Interface and turn off the DHCP there. And make sure to change the IPv6 settings there as shown in the image below.
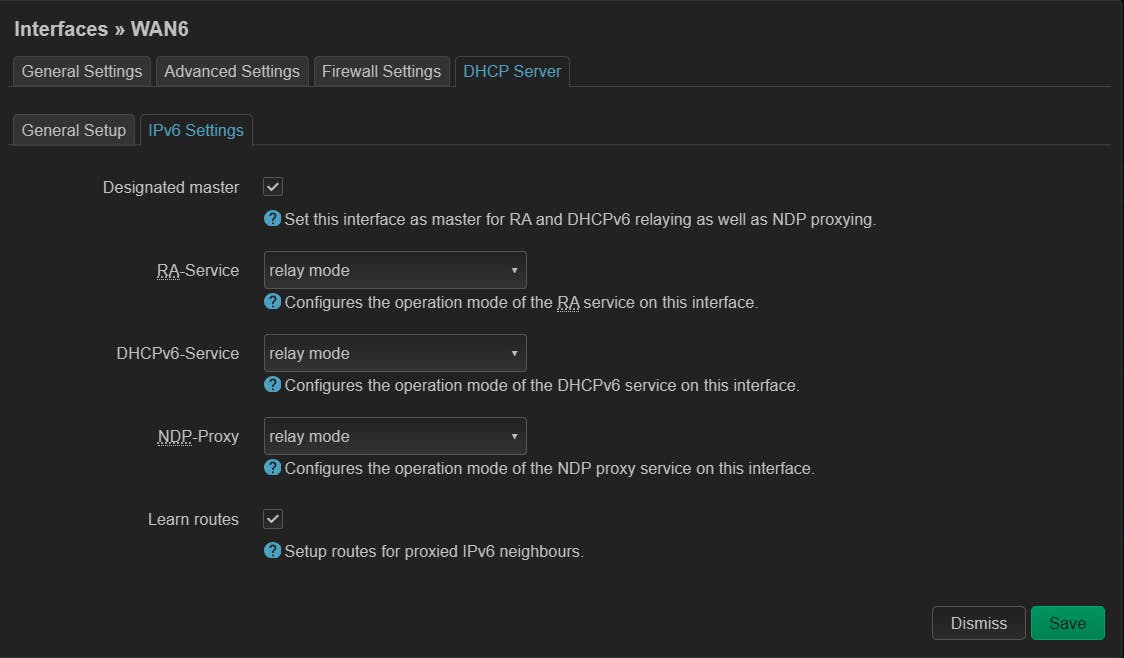
With that done, save it. And now head over to the LAN Interface. Edit the interface and go to it's DCHP Server Option and there make changes to the IPv6 settings as shown in the image below. You can skip the IPv6 DNS Server and leave it as it is.

Now with that done. Save the changes and reboot your router. And you should start seeing your devices getting IPv6 assigned directly from the main CPE.

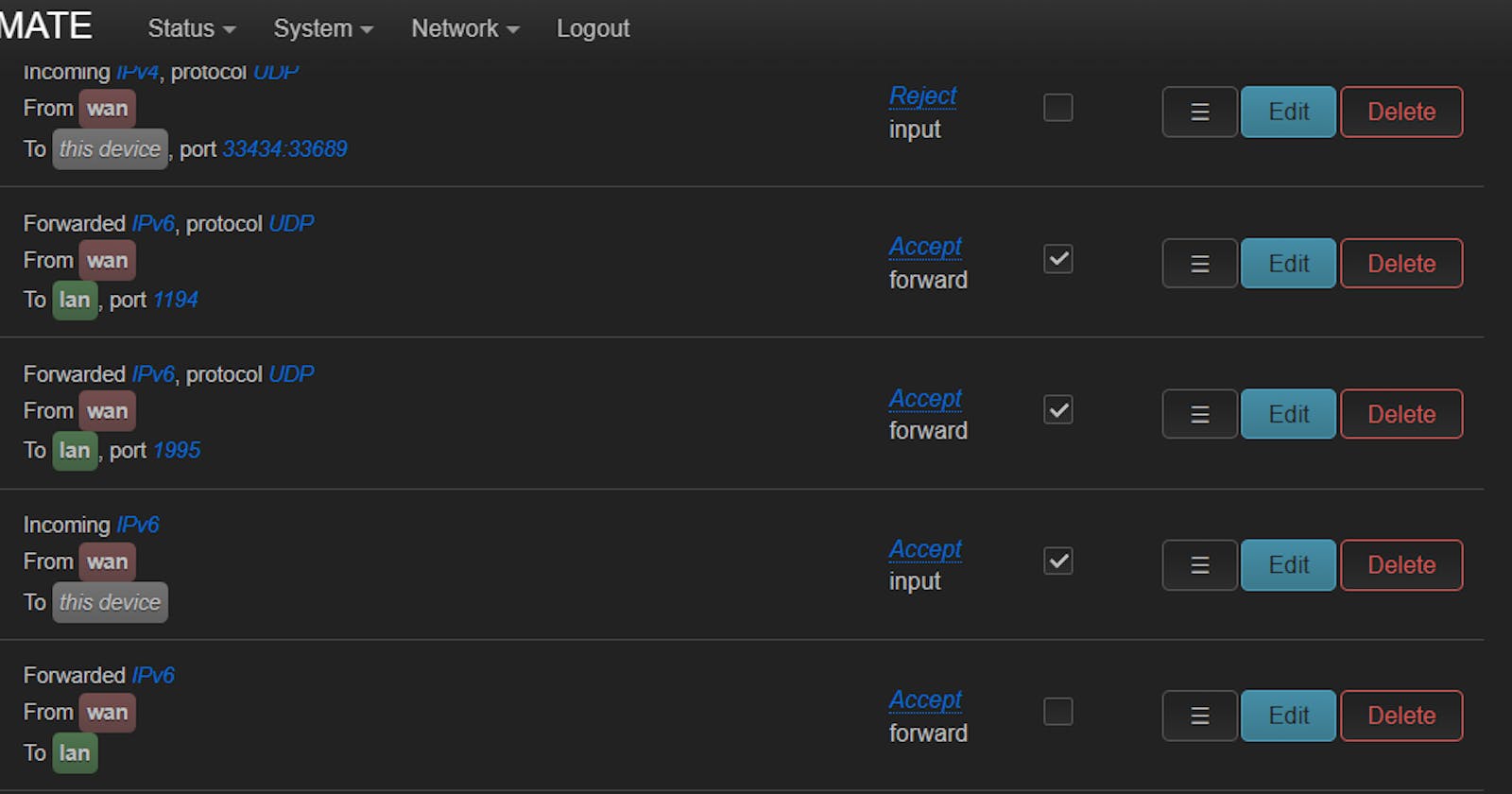
Now that's done. While exposing a port, you need to first allow that port from the firewall settings on your router. You can do that by heading over to the Firewall settings under the Network tab.

As you can see here, I have allowed the UDP protocol with ports 1195 and 1194. Those are for the VPN Server that I am hosting on my Linux servers. With that done those ports will be accessible by other IPv6 users.